
TVN Tech | Remote Work Raises New Cybersecurity Threats

Cybersecurity challenges increased when the coronavirus pandemic prompted broadcast teams to work from home, in some cases with equipment not owned by the news organizations.
Broadcasters have long relied on virtual private networks (VPNs) to provide news teams remote access into the organization’s network, but a surge of work-from-home users accessing the VPN at once can cause bandwidth constraints. At the same time, not every user should have access privileges to all parts of the network.
Threats to cybersecurity come from within and without, and experts advocate the use of layered defenses to protect the network. Because disgruntled employees can cause trouble, vendors are offering behavior analytics to flag unusual employee behavior patterns. Other major threats to broadcasters’ cybersecurity programs come in the form of phishing and malware, and methods of attack are constantly evolving. As one expert puts it, cybersecurity is not “one and done,” but requires ongoing effort.
When stay-home orders began rippling across the nation earlier this year, some broadcasters like WGBH in Boston had already put a lot of remote-work tools in place.
“In most cases, WGBH was in a good position to manage” having the majority of the team working remotely, says Shane Miner, CTO at WGBH. “A lot of broadcasters had to scramble to get the tools. We’d dabbled enough to feel comfortable.”
The WGBH team uses a shared edit environment that editors can access from home via virtual desktop infrastructure (VDI). While those have “been good for us,” Miner says, “we’d love to see the efficiency and performance of those improve.”
WGBH purchased the VDI hardware a few years back, and it was scoped to handle about a dozen editors working remotely at the same time, not the 40 or so employees who currently need the system at the same time.
“It does a reasonable job, but the longer we live on it, we know we need a major upgrade or a change,” he says, noting he is evaluating what a major on-prem VDI upgrade would look like versus a cloud upgrade.
The security of the current system is the same as if the editor were working in the building, he says.
Secure Remote Access
Hubbard Broadcasting Eric Neel, corporate’s director of IT infrastructure, says the fundamental cybersecurity requirement during the pandemic has been maintaining secure remote access.
“The tools we had selected over the last year happened to lend themselves toward remote workflows. We’ve benefited from the timing in our own choices. We just had to buy a lot of laptops in a hurry,” Neel says.
Hubbard uses VPN technology and permits only company-provided equipment to access the network and conduct business.
“We’ve seen the expansion of the end points that historically were living inside our network are now suddenly living in people’s homes,” which raises the challenge of managing those end points and end-point security, Neel says.
By using only company-provided equipment, it’s possible to eliminate the liability associated with use of personal equipment and minimize basic security exposures, he says.
Neel says VPNs and securely managing the end points are the two major components of addressing the biggest cybersecurity challenges the broadcaster has.
Hubbard was fortunate, Neel says, because the company was “just rolling out” a system that allowed remote access as people were starting to be ordered to stay home. The pandemic did “force us to accelerate the adoption of different tools.”
Such tools include those supporting the help desk, security patching, reporting on the health of certain systems and reacting to those health reports. Hubbard is using multiple layers of cloud-based virus and malware detection systems along with tools that help ensure secure access to the internet.
Hubbard uses Arctic Wolf as a third-party service to monitor the network and review security events on the networks, servers and end points, Neel says.
“It was like hiring a security operations center,” he says. “They’re an extra set of eyes helping us keep tabs on the health of the end points.”
Old Challenges Remain
While the COVID-19 pandemic has changed where and how broadcasters are working, the basic need for cybersecurity remains.
As Rob MacDonald, director of solutions marketing at MicroFocus, puts it: “The challenges haven’t changed. Regardless of whether you’re working remotely or in the office, the net result is people are still trying to get into your stuff, there are still potentially employees who are upset or unhappy or do things they don’t realize they shouldn’t do.”
Security must always be top of mind, he says, because “bad guys are always finding new ways to exploit things and … find that next hole to get into the ecosystem.”
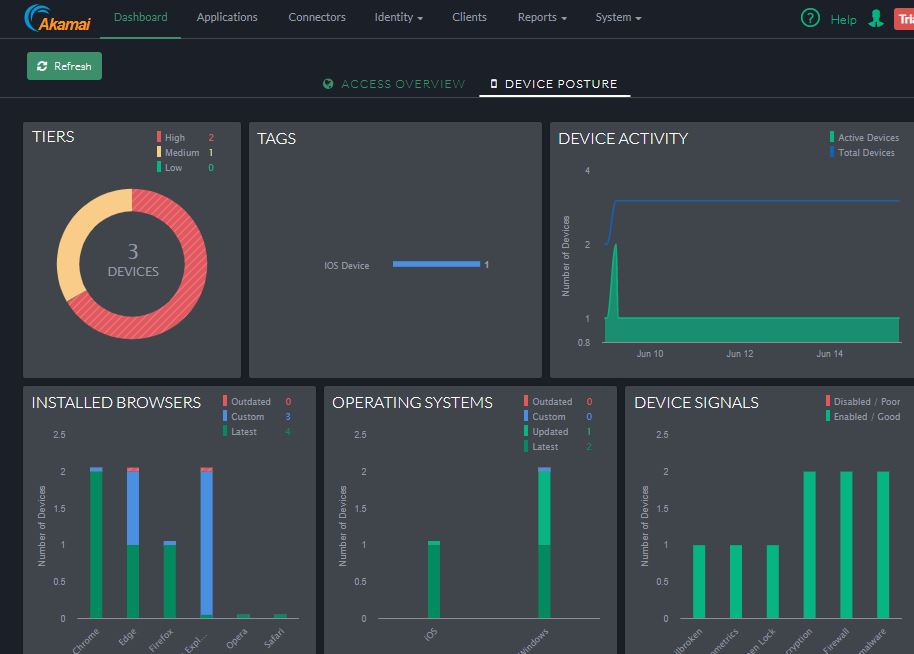
The dashboard of Akamai’s Enterprise Application Access, which gives administrators visibility into all of the components involved in secure access. Enterprise Application Access’s cloud architecture closes all inbound firewall ports, while ensuring that only authorized users and devices have access to the internal applications they need rather than the entire network.
Jim McGinn, executive lead of Infinitive’s technology practice, says organizations tend to take cybersecurity for granted until it’s too late, claiming it’s too expensive or that no one would try to steal their information.
“Sometimes it takes an attack and maybe negative press for a company to take it seriously,” McGinn says.
The cost of a cyber breach is tremendous, he says, in terms of both loss of consumer trust and dropping stock prices.
And a cyberattack on a broadcaster that disrupts the operations of the media could be damaging to the country from a national security perspective, according to Parham Eftekhari, SVP and executive director of the Cybersecurity Collaborative.
He suggests a possible scenario where cyberattackers hacked a major network’s email system and leaked confidential sources or information that might affect the current presidential election.
Protecting user credentials is critical to protecting the overall security of the network, Eftekhari says. One step of that is scrutinizing the credential and access management strategy so the user has access to “the right types of information,” he says.
In a situation where an employee is using a personal device, he says the insider threat vector increases because a family member or roommate may have access to the same company records through that laptop.
“A lot can be done to secure the data,” such as better segmenting it so that “if a credential is compromised because of a successful phishing attack or adversarial attempt, the data on your network is segmented in a way they’re not able to access all of your data,” Eftekhari says.
Limiting Network Access
Providing access to only the right parts of the network is a key part of the cybersecurity picture, says Tony Lauro, director for security technology and strategy at Akamai.
In a traditional remote access model with a VPN, a user name, a password and a certificate on the computer will allow the user into the network.
“For years, we’ve known that’s an area where hackers like to target,” Lauro says.
Multi-factor authentication can secure the network, but the problem is the range of network access granted through the use of the VPN, he says. A hacker can use the credentials of a user who has been successfully phished to gain access to the broadcaster’s network and plant ransomware or cause other problems, he says.
“Just because someone provides a username and password doesn’t mean they should get access,” Lauro says.
A zero-trust networking model can assess a device and validate that it meets update criteria and the user identity based on details known about the user, such as normal log-in location and time to flag potential issues, he says. A zero-trust remote access model will provide access to a certain piece of the network without access to the rest of the network, basically isolating the connection to a specific application, he says.
“It gives you just enough access to do what you need to do for your job, not giving access willy-nilly that you don’t need,” Lauro says. “Every application and every user are paired together based on need-to-know for the job function.”
At the beginning of the pandemic, more broadcasters were buying additional access to VPNs, he says, but lately have begun “righting the ship” by transitioning to zero-trust principles.
Akamai offers Enterprise Application Access as its solution for zero trust for remote access.
Behavior Analytics
Behavior analytics, which draws on the power of artificial intelligence, is another piece of the cybersecurity puzzle.
MacDonald says behavior analytics can be used to verify a user is doing what it should be doing based on details about the user’s identity. Behavior analytics can be used to flag behavior outside the norm, making it possible to eliminate false positives and focus on and respond to true security threats by shutting down access, he says.
“The more we know about these identities and devices, the higher level of security we can actually provide,” he says.
There can also be a predictive element to behavior analytics, McGinn says. Pairing artificial intelligence with behavior analytics can help sift out internal threats, he says. It’s possible to track websites where people are communicating dissatisfaction or unhappiness, such as in Zoom chats, to build up an insider threat portfolio.
“Is Bill Smith planning to leave the company? Is Mary Jo working on information and printing stuff out and taking information she’s not supposed to have? Is anyone trying to steal IP or trade secrets? Is there an employee feeling like he’s going to be fired who might do something malicious on a corporate network?” McGinn asks.
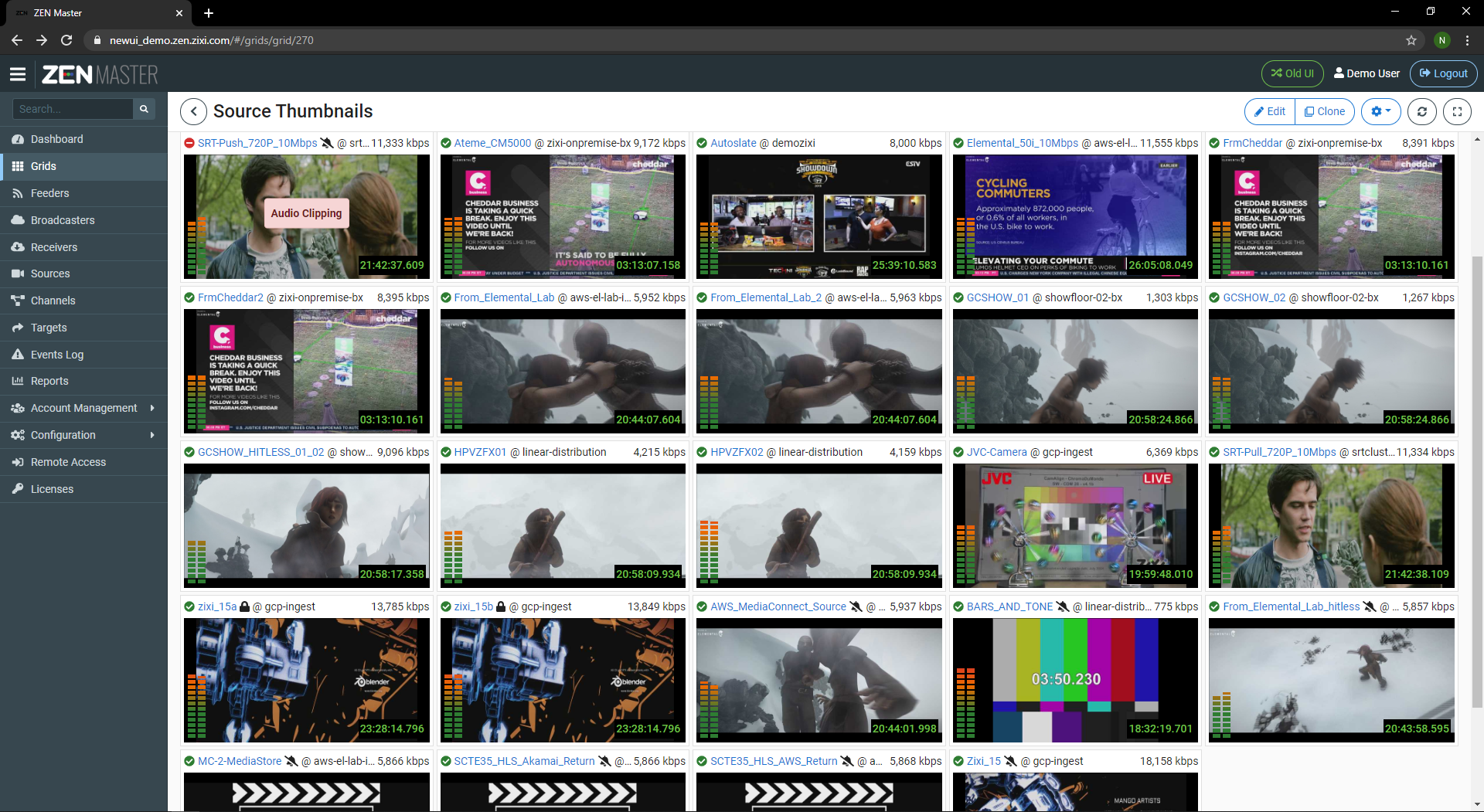
Zixi’s ZEN Master, a cloud-based virtual control plane for Zixi’s live streaming platform, showing the grid display, allowing users to view live stream status and health in real-time across Zixi workflows.
Layered defenses are a preferred protection method in cybersecurity, and Eric Bolten, Zixi’s VP for business development, says they are one of the chief reasons live feeds are difficult to disrupt.
In the virtual world, the production control room uses password encryption, permission-based roles that restrict access, session control and other security measures, he says. “There are a lot of different ways to ensure you can’t be hijacked. Gaining access to a livestream is quite difficult.”
Phishing Threats
One of the major cybersecurity vulnerabilities for broadcasters is phishing, often posing as email from someone the employee knows, but containing nothing but a link. Clicking the link can introduce malware, allowing a virus to propagate through the corporate environment and possibly taking down key infrastructure, McGinn says.
Because it’s such a huge threat, Miner says WGBH does simulated phishing training to help users know what to look out for.
Eftekhari says “good cyber hygiene” includes “think before you click” because phishing is the No. 1 cause of incidents in cybersecurity. “Be vigilant that you are a target. There are adversaries actively trying to gain access to your credentials, penetrate your organization and exploit the data you host.”
Organizations prioritizing cybersecurity will properly support the cybersecurity teams, fund them properly, include cybersecurity experts in the IT team and “empower them to build and execute a layered strategy” to protect data and defend the organization, Eftekhari says.
Just installing a technology or tool to solve a problem doesn’t mean a broadcaster can “stop and sigh with relief and go about their business,” MacDonald says. “You can’t stop. There’s always something going on.”
In fact, while many are excited about the high speed 5G network, it’s a two-edged sword.
The bad guys are “going to be able to attack organizations from anywhere with incredible speed,” MacDonald says. The evolution of cellular technology “allows us to work faster at home but allows the bad guys to do things faster than they could three years ago. That’s going to be a fact of life for the foreseeable future.”
Another fact of life, he observes, is that end users are going to do whatever is easiest for them.
“We have to make security requirements easy enough that people won’t bypass it,” MacDonald says. “If we make the security difficult for them to do, they’re going to look for the easiest way to bypass it.”
After all, he says, “security is only as strong as the person that’s using it.”






























Comments (0)