
TVN Tech | Broadcast Hackers Drawn To Email Targeting

Broadcasters are especially enticing targets for phishing. Software prevents most email attacks, but training humans not to click suspect links remains essential.
Email is one of the main methods attackers use to gain entry into a broadcaster’s network, and attackers aren’t always motivated by money. Some would-be attackers are nation-states interested in influencing news or politics, while others are “hactivists” aiming to spread their own messages. Email attacks include basic “spray and pray” phishing attempts and targeted spear phishing efforts that rely on social engineering to encourage the recipient to click on a link that ultimately gives an outsider control of the computer.
A number of different software programs work to keep these suspect emails out of inboxes, but attack methods change quickly. When phishing attacks do slip through, it’s incumbent on recipients to use common sense before taking action on an email that seems, on the face of it, to be a reliable source making a reasonable request. In the end, experts say, the cost of a successful attack on an organization’s reputation far outweighs the cost of prevention.
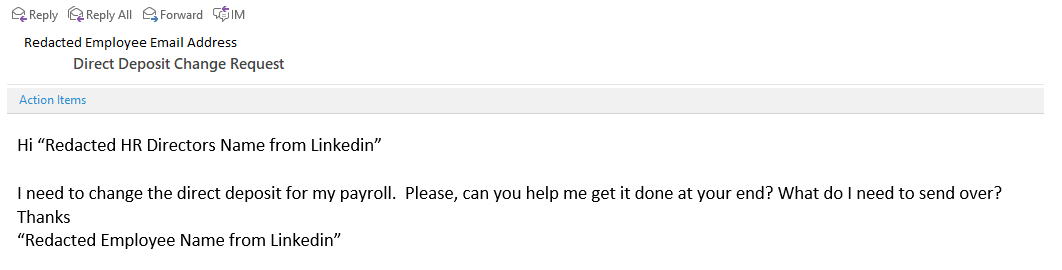
More sophisticated phishing attempts use social engineering, in this case to get someone in HR to change the routing number for an employee’s direct deposit. (Source: Mimecast)
When it comes to email, the only thing that matters is the motive of the person trying to get to you, says Trace Hollifield, senior security architect, Southeast at GuidePoint Security, a cybersecurity company that works with five main email security vendors.
And broadcasters are more vulnerable to cyberattacks than other average companies of their size due to their unique role in society, according to Matthew Gardiner, principal security strategist at Mimecast.
Nation-states, hactivists and money-motivated attackers are all likely to target broadcasters, he says, and “email is a good way for all three groups to accomplish what they’re trying to accomplish.”
As such, he adds, broadcasters need to follow best practices for cybersecurity even more than other companies of similar sizes.
Email Threat Types
Email threats come in a few key styles.
The first is what Joel Sloss, senior program manager for Microsoft Azure M&E Security and Compliance, calls a typical email threat.
“It’s general. It’s, ‘Hey, I’m a prince of Nigeria. Send me $5,000 and I’ll send you a million dollars in three days.’ It’s trying to extract information out of you,” he says.
Hollifield says a second style of phishing also casts a wide net to see who it can catch. This attack may be an email claiming a package from Amazon is being delivered and that allows the recipient to click a link to check the status. Such an email is a “doppelganger” of what the real message looks like, he adds.
“It’s so common, and people fall for it. They don’t remember ordering, but they click on it to see what the status is, and boom. They get infected,” Hollifield says.
An even more advanced form of phishing may look like a service that the person subscribes to or may even look like it’s coming from someone the recipient knows. These attacks, Sloss says, use some amount of social engineering and often include some previously compromised data in their effort to get the recipient to click.
The most targeted email attacks are referred to as spear phishing and are a “concerted effort to get at an individual, whether a C-level executive or someone influential or with access to sensitive information,” Sloss says.
In such a case, he says, the attackers are “crafty” about how they put the email together. It will look like it comes from a colleague or a trusted source, he says, and when the recipient responds, they often provide “just enough information” to help the attacker “break down security layers. This happens often to system administrators. Often they’re the first to get compromised. Once they get admin access, it’s game over.”
Advances In Socially-Engineered Attacks
Sloss says there have been “big advancements” in the last couple of years in the sophistication of spear phishing and social engineering.
“We are enabling the hackers to do it. People are publishing stuff online all about themselves, and all that can be used to social engineer,” Sloss says. “This makes it that much easier for those guys to target you and be successful. Social engineering attacks are the most dangerous.”
According to Tony Lauro, director of security technology and strategy at Akamai, the basic thing about social engineering is that it appears to give a pretext for the emailer — often a bad guy impersonating someone the recipient knows — to reach out to the recipient. In short, he says, it gives a reason, or trigger, for the recipient to respond.
“It claims, ‘I’m the CEO, and this is urgent,’” he says. “I’ve lived through it. I’ve seen a bogus message come from the CEO.”
Such emails, Lauro says, may ask someone to forward employee W2 information or for the finance people to send money to an account because a merger is moving forward.
“It’s somewhat believable” and the person could fall for it, Lauro says.
Gardiner says the attackers make it look believable and “lay out the email to look the way they want, attach files, put in links. It’s a dream from an attacker’s point of view, to reach into any organization and … get the receiver to do what they want to do.”
He adds, “A bad email … needs people to engage with it, to click a link, open a file,” Gardiner says.
The Filtering Defense
But if the potential victim never sees the email? That’s a win.
“The vast majority of malicious email can be caught before it’s delivered,” Gardiner says.
Filtering is a first line of defense. Hollifield says an estimated “95% of all email floating around on the internet is spam and trash. There are billions of messages that nobody ever pays attention to or sees.”
Mimecast is a cloud-based service that filters email and applies security analytics and policies to keep attacks from reaching the intended recipients.
“We get billions of emails each month on behalf of our customers,” Gardiner says. And the company applies natural learning and artificial intelligence to constantly refine its filtering methods. “The more emails you see, the more bad emails you see, the quicker your system can become intelligent.”
Sloss says Outlook, included in Microsoft 365 and running on the Azure platform, can provide enterprise functionality and security to companies, large or small. However, he says, “no single action” is going to protect an organization. They need a multilayer strategy that addresses viruses, scans attachments, has a strong firewall and educates users, he says.
Akamai’s Enterprise Threat Protector carries out recursive DNS inspections and looks up links in email to ensure the links are safe.
“It analyzes threats before your computer has a chance to connect to them. It happens in the background. The user is not affected,” Lauro says.
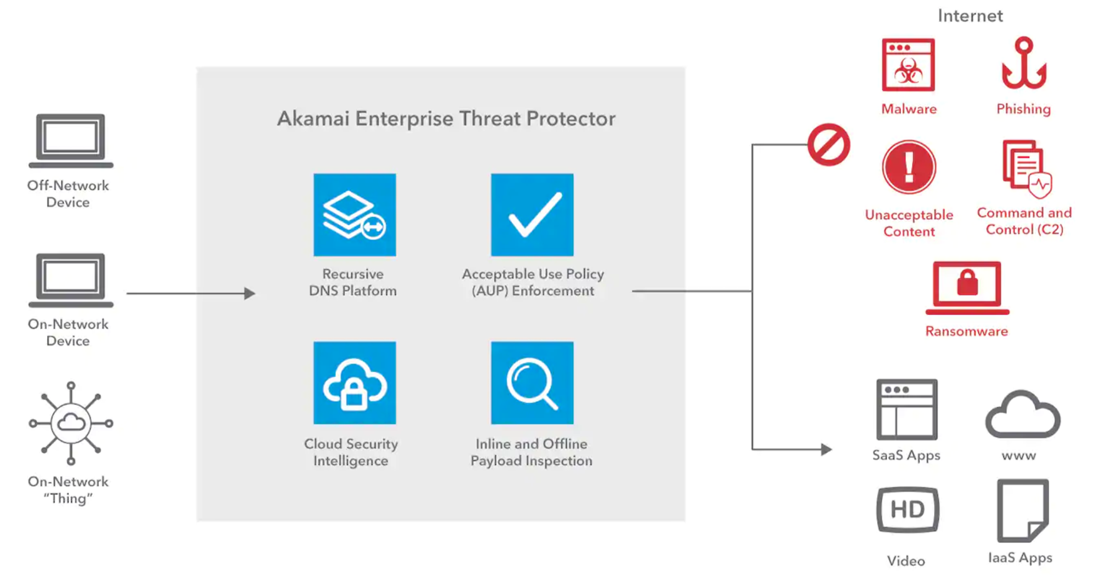
Akamai’s Enterprise Threat Protector is a cloud-based secure web gateway that enables security teams to ensure users and devices can safely connect to the Internet, regardless of where they are connecting from, without the complexity associated with legacy, appliance-based approaches.
Healthy Practices
Gardiner says that while no program is a silver bullet when it comes to security, a set of good practices that include detection of things that have gone wrong and recovery methods to repair problems expediently can go far in maintaining a broadcaster’s email security.
Those good practices include keeping system patches up to date; monitoring network and email traffic for malicious or anomalous activity; and maintaining good backups of systems to allow for recovery in the event of a successful ransomware attack, Gardiner says.
If a broadcaster handles prevention, detection and response “pretty well, the chance of getting badly hit goes down pretty dramatically,” he says.
The security system needs to be “as easy as possible for the user community to comply with because nobody wants to screw over their employer,” Sloss says, “but the harder you make it for them to comply, the less likely they will cooperate and the more likely they are to find a purposeful way around it.”
Importance Of User Education
While much of email security can be automated, user education cannot, and it remains one of the most critical elements in the email security plan.
As Hollifield puts it, the human is always “the weak link in the chain regardless of what security systems are in place because they’re always one click away from a bad thing happening. When you click, you give permission to do an action. You can empower bad guys to take over your system,” Hollifield says. “Don’t invite the vampire into your house. That’s when bad things happen.”
Hollifield says the “burden of a breach is amazing” and could be a career-ending or business-ending mistake.
While companies depend on email, the cost and level of expertise necessary to secure it may be “beyond the ability of your average company,” Gardiner says. “That’s why the cybercrime business is so profitable.”
It’s also one of the reasons so many cybersecurity and email security companies exist — to serve as a second pair of eyes for organizations and help them reduce risks, Hollifield says.
Gardiner says it surprises him how many organizations have fallen prey to phishing problems that later fail to use best practices to defend themselves. The time to defend the organization is before the attack, he says.
“You don’t wait until you’re sick to get vaccinated,” he says. “You make a best practice attempt to stay healthy. It’s the same thing in cybersecurity.”
Email remains one of the main ways through which attackers gain entry into broadcasters’ networks, and they change their methods of attack quickly. Good training not to click on suspect links is an essential defense. Click To Tweet





























Comments (1)
rosaliesteame says:
January 28, 2024 at 5:20 am
Business email is more difficult to hack. Developers of email services are aware that business correspondence can be much more attractive to hackers than private correspondence, as it allows them to gain access to financial documents, business projects and trade secrets. In addition, special business mail directly affects the improvement of the deliverability of letters in general, I advise you to study this issue in more detail here https://sh.consulting/blog/email-deliverability